Introduction
Fraud is a growing concern for businesses worldwide, leading to financial losses, reputational harm, and regulatory issues. According to the Association of Certified Fraud Examiners (ACFE), organizations lose an estimated 5% of revenue annually due to fraud.
A Fraud Risk Assessment (FRA) and a Continuous Monitoring Program (CMP) are critical tools in detecting and preventing fraud. This blog will break down these concepts, outline step-by-step processes, and provide real-world examples to help organizations protect themselves from fraudulent activities.
Understanding Fraud Risk Assessment (FRA)
A Fraud Risk Assessment is a proactive approach to identifying and evaluating potential fraud risks in an organization. It helps businesses recognize vulnerabilities and implement preventive measures to mitigate fraud.
Key Components of a Fraud Risk Assessment
- Risk Identification:
- Identify areas within the organization most susceptible to fraud.
- Analyze past fraud cases, industry-specific threats, and regulatory requirements.
- Example: A company operating in the e-commerce sector may face higher risks of payment fraud and chargeback schemes.
- Fraud Scenario Development:
- Develop potential fraud scenarios based on real-world cases.
- Example: An employee could create fake vendor invoices and authorize payments to personal accounts.
- Risk Prioritization:
- Assign risk levels based on likelihood and impact.
- Example: Payroll fraud may be categorized as a high-risk area due to its financial impact and ease of execution.
- Control Evaluation:
- Assess current controls such as segregation of duties, approval workflows, and automated alerts.
- Example: If an organization lacks a dual-approval system for large transactions, it may face a higher fraud risk.
- Reporting & Documentation:
- Document all findings and communicate them to senior management.
- Use heat maps, dashboards, or reports to visualize high-risk areas.
Step-by-Step Guide to Implementing a Fraud Risk Assessment (FRA)
Step 1: Establish a Fraud Risk Committee
- Form a team of internal audit, compliance, finance, HR, and legal professionals. This is solely dependent on the size and structure of the organization.
- Clearly define roles and responsibilities.
- Ensure senior management and board involvement.
Step 2: Conduct Fraud Awareness Training
- Educate employees on different types of fraud and ethical standards.
- Implement an anonymous whistleblower hotline.
- Example: A company that trains employees to recognize invoice fraud can detect irregularities faster.
Step 3: Develop a Fraud Risk Universe
- Identify and list all key business processes at risk of fraud.
- Use the ACFE Fraud Tree to categorize fraud risks (e.g., corruption, asset misappropriation, financial statement fraud).
- Example: A procurement process may be at risk of kickback schemes between vendors and employees.
Step 4: Assess Likelihood and Impact
- Rate fraud risks using a structured scoring system:
- Likelihood: Rare, Possible, Probable, Certain.
- Impact: Minor, Moderate, Severe, Catastrophic.
- Assign ownership of each risk to relevant departments.
- Example: Vendor fraud in high-value procurement deals may be labeled as “Probable” with a “Severe” impact.
Step 5: Design & Strengthen Control Measures
- Implement preventive controls (e.g., dual approvals, vendor authentication, system alerts).
- Introduce detective controls (e.g., data analytics, surprise audits, whistleblower mechanisms).
- Example: A company implementing real-time transaction monitoring can detect unauthorized payments before processing.
Step 6: Regularly Review and Update the FRA
- Conduct an annual assessment or when significant organizational changes occur.
- Adapt to emerging fraud risks (e.g., cyber fraud, AI-generated fraud schemes).
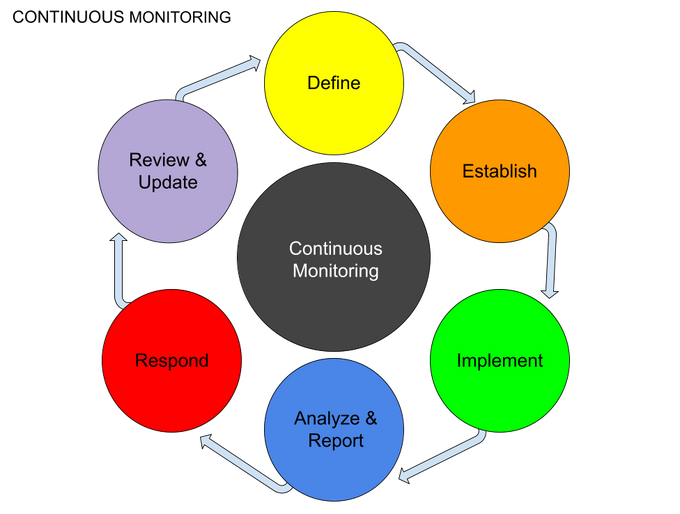
Understanding Continuous Monitoring Program (CMP)
A Continuous Monitoring Program (CMP) uses real-time analytics and automation to track transactions and identify fraud indicators as they occur.
Benefits of Continuous Monitoring
✅ Early fraud detection using AI and predictive analytics.
✅ Cost reduction through automated fraud detection.
✅ Regulatory compliance assurance.
✅ Operational efficiency through reduced manual oversight.
Step-by-Step Guide to Implementing a Continuous Monitoring Program
Step 1: Define Monitoring Objectives
- Determine what data and activities need to be monitored.
- Example: High-risk transactions, vendor payments, and policy violations.
Step 2: Choose Monitoring Tools & Techniques
- Use data analytics platforms (e.g., ACL, IDEA, Power BI, Tableau).
- Implement machine learning algorithms to detect anomalies.
- Example: A machine learning tool detects an employee making frequent high-value refunds to personal accounts.
Step 3: Develop Monitoring Scripts & Algorithms
- Create scripts to detect fraud triggers, such as:
- Sudden changes in vendor bank details.
- Employee expense claims exceeding policy limits.
- Duplicate invoice submissions.
- Example: A bank flags unusual cash withdrawals from dormant accounts as a potential fraud indicator.
Step 4: Automate Alerts & Reporting
- Implement real-time fraud dashboards.
- Set up automated alerts for high-risk transactions.
- Example: A retail company receives an alert when multiple refunds are issued to the same credit card in a short period.
Step 5: Investigate Suspicious Activity
- Assign fraud alerts to investigators.
- Conduct forensic audits for high-risk red flags.
- Example: A manufacturing firm investigates a sudden spike in raw material orders from a single supplier.
Step 6: Continuous Improvement
- Regularly update monitoring scripts based on fraud trends.
- Use post-incident reviews to improve detection capabilities.
- Example: A travel agency refines its fraud detection algorithms after identifying fraudulent customer bookings.
Real-World Case Study: Preventing a $5M Fraud
A multinational retailer implemented a continuous monitoring system that flagged an unusual inventory adjustment pattern. Upon investigation, internal auditors discovered a scheme where warehouse employees manipulated stock records to steal high-value electronics. By using real-time alerts and data analytics, the company prevented a $5M loss and strengthened internal controls.
Conclusion: Why FRA and CMP Are Critical for Businesses
To stay ahead of fraudsters, businesses must:
✔ Conduct regular Fraud Risk Assessments.
✔ Implement real-time monitoring systems.
✔ Use AI-driven data analytics for fraud detection.
By integrating Fraud Risk Assessments with Continuous Monitoring Programs, organizations can create a robust anti-fraud framework that mitigates risks, reduces losses, and enhances compliance.
References
- DiLorenzo, C. (2015). Creating a Fraud Risk Assessment and Implementing a Continuous Monitoring Program.
- ACFE Report to the Nations (2024).
- COSO Framework (2013).
- Sarbanes-Oxley Act (2002).
- Top Strategies for Detecting and Preventing Fraud in Organizations